The OBO problem: who’s really acting on your behalf?
The future of employee digital trust means knowing who's acting ‘on behalf of’ your business
Hi everyone, thanks for coming back to Customer Futures.
Each week I unpack the disruptive shifts around ‘Empowerment Tech’. Digital wallets, Personal AI and digital customer relationships.
If you haven’t yet signed up, why not subscribe:
Hi folks,
Another deep dive for you.
Because we don’t talk enough about employee identity, or Know Your Employee (KYE).
More specifically, we don’t talk enough about the digital risks around employees. When and how they interact. When and how they transact. And when and how they sign things on behalf of the business.
Because often the real business risk isn’t what is being signed.
It’s who is signing it.
If you start paying attention, there are digital risks and fraud issues everywhere with employee ID.
Yes, there’s an exciting conversation happening at the moment around digital identity. Around digital wallets. And even how we can use AI Agents to automate tasks for workers.
But do we really know which business is which? Which division? Which employee? How do we know? Which sources do we trust?
Everyone is now working more globally than ever. More remotely than ever. And more digitally than ever. If we can’t prove who our employees are ‘out in the wild’, how on earth are we going to trust AI agents?
So today’s post looks at:
Who really signed that document?
The illusion of control
‘OBO’ as a new layer of employee identity and trust
Enhancing and extending ‘IAM’
Mapping the different zones for ‘On Behalf Of’
From one-off access to portable authority
Lots to dig into.
As ever, it’s an opportunity to explore the future of being a digital customer. So welcome back to the Customer Futures newsletter.
Grab your favourite hot drink, a comfy corner, and Let’s Go.
Who really signed that document?
I’ve been working with the team at Digidentity on a deceptively simple, but critical question: What happens when an employee acts on behalf of an organisation?
It’s a much harder problem than it appears.
Why?
Because you need to know the organisation being represented. You need to know the individual performing the action. And you need the employee context. Is this about a signature, a financial approval, or acting in a regulatory capacity?
But then, even if you know all those things, how do you know they are still true in that moment?
You see, many employee risks happen after someone is hired.
As new joiners progress and change roles. As they take on additional responsibilities. And as they exit the business. Their authority evolves, often without being tracked and verified, or their access revoked.
Yes, many IT and HR systems handle updates to role changes. But many don’t. And which systems today can manage transactions and employee authority beyond the business?
We need to start thinking about employee identity - and indeed organisational identity - in a new way. Not just as a business registration number to be added to a form. Or an employee’s login credentials.
But rather as a system of dynamic trust.
One that protects the business and the employee in the moments that matter, both inside and outside the company walls.
The illusion of control
In most companies, employee identity is a static snapshot.
‘KYC’, ‘KYE’, and onboarding processes are pretty much part of an HR checklist. Useful for day one, but are they ever revisited?
Meanwhile, employees are constantly in motion:
They move across departments
They take on new responsibilities
They approve suppliers and sign NDAs
They submit filings and represent the business at external events, including with regulators
Now ask yourself:
What happens when a former employee signs a contract after they’ve left?
What if someone approves a purchase they’re no longer authorised to make?
What if an employee walks onto a partner site, and can’t prove who they are or what they’re authorised to do?
What if an auditor asks for proof that a staff member had the right authority, and there’s no evidence?
These things have always been thought of as IT and ‘Identity and Access Management’ (IAM) problems. About who can log in, and who has access to what. But many organisations are still operating on old assumptions:
Employee identity means an email address, payroll ID, and maybe an employee account number
Org ID means an entry in a government registry, or a Dunn and Bradstreet number
Authority mostly means a job title
Trust means a name on a document
But roles can change dynamically. Businesses and departments can morph and merge. And, especially in the age of GenAI, signatures can be spoofed. Things like login and access management say little about who someone represents.
Flipping the risk
Let’s bring it to life. Lets look at electronic signing tools like DocuSign or Acrobat.
Today, if someone digitally signs a PDF, do you really know who signed it?
Nope.
In fact, did you know that if it goes to court, it’s the recipient’s responsibility to prove that the digital signature was from the right person? That it really was Jamie who signed the PDF, and not someone else using his laptop?
Helpfully, there is now a highly trusted way to prove a person’s identity in those transactions. It’s using a ‘Qualified Electronic Signature (QES). Before you can sign a document using a QES, you must have completed a certified ID check.
OK, so why all the hoopla just for signing a document?
Because if a document is signed using a QES, the burden of proof shifts to the signer. Meaning that in a court of law, if you challenge a digital signature, the person who signed the document must now prove it wasn’t them signing.
That’s a 180-degree shift away from ‘anyone could have signed this’. And a complete reversal on the company risk register.
OK, with QES, we now know that it’s Jamie signing a document. But how do I know who Jamie represents?
That kind of assurance demands something more than static records. You now need to know:
Which organisation is being represented (KYB)
Which individual is taking action (KYE)
The specific context - what’s being done, why, and with what authority
Welcome folks, to the new standard in employee assurance.
Also known as ‘OBO’.
OBO as a new layer of employee identity and trust
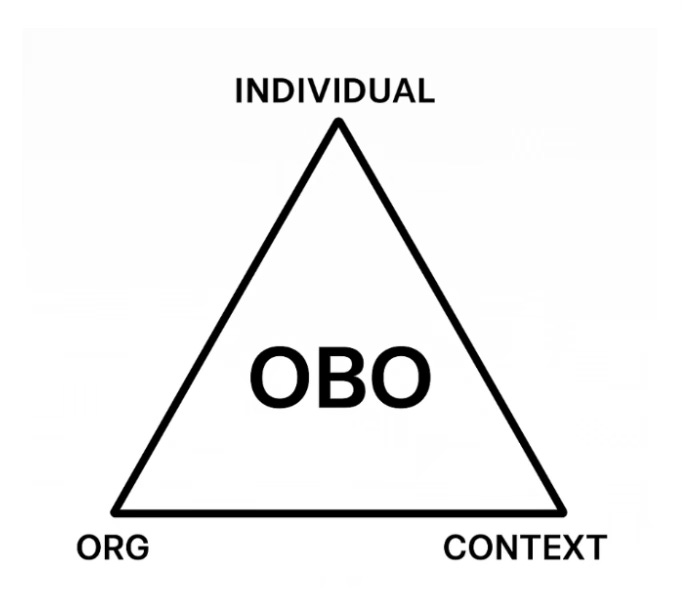
OBO is short for ‘On Behalf Of’.
And it allows an individual to act with verified authority, in context, on behalf of an organisation.
Critically, OBO carries that authority across platforms, roles, and over time.
And it brings three things together:
The organisation being represented
The individual taking action
The specific context
At the centre is the OBO relationship. Verifiable, portable, and auditable. Once you have all three parts confirmed - connecting the organisation, the person, and the permission - you can produce an ‘OBO credential’.
Enhancing and extending ‘IAM’
I can already here some of you shouting. Isn’t this already covered by ‘IAM’?
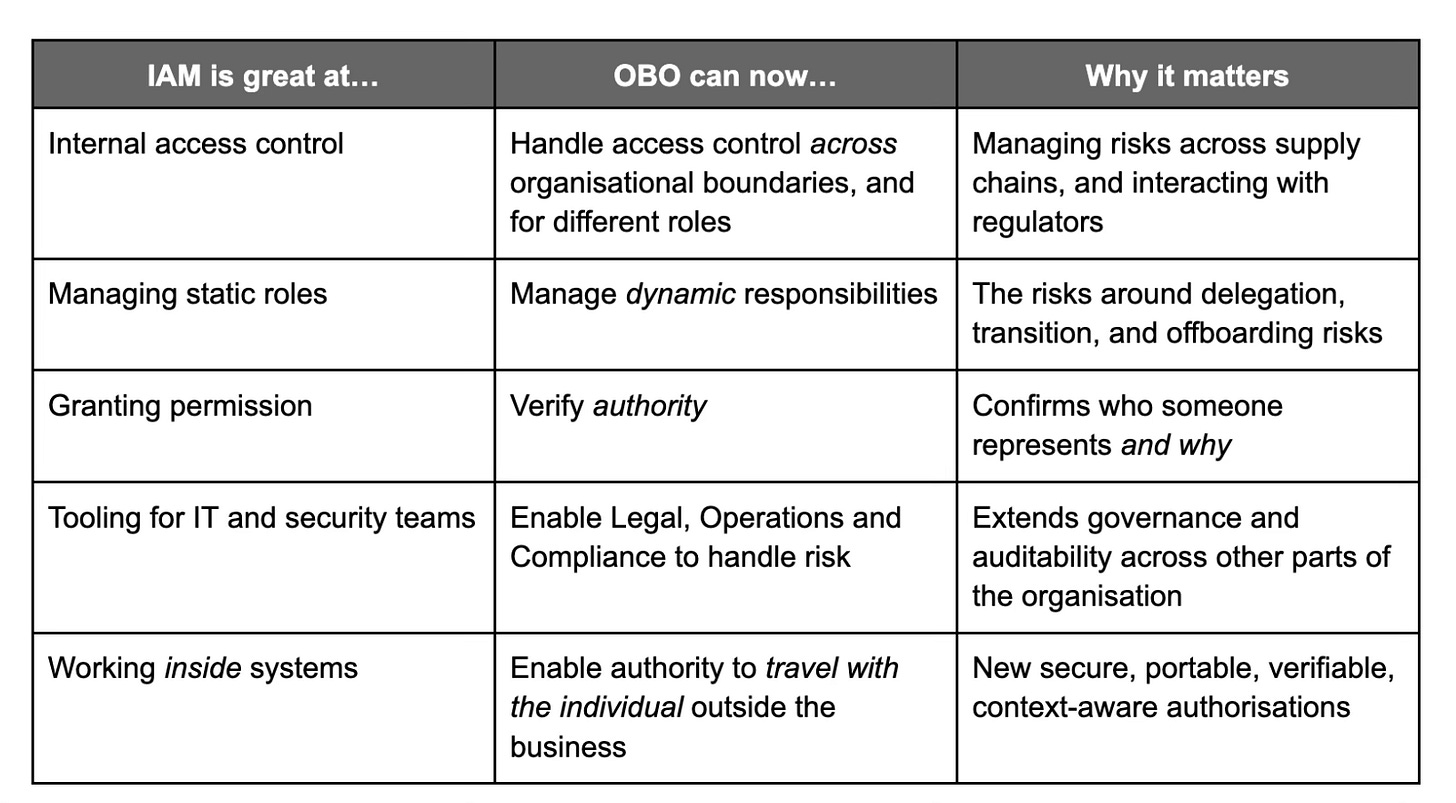
Yes, many large organisations already use IAM (Identity and Access Management) systems to control who can access what internally. Quite rightly.
And IAM is brilliant. Because it helps businesses:
Onboard users
Assign permissions
Restrict access to sensitive resources
Log activity inside their IT environment
But IAM was designed for internal control, not external representation.
It tells you “This person can access this system.” But it doesn’t tell you “This person is currently authorised to represent our business to others, and here’s the verifiable proof.”
Here’s one way to think about it:
OBO has the potential to handle the real-world complexity of evolving tasks, fuzzy job boundaries, shifting department structures and changing roles… but also cross-company interactions.
In fact, Microsoft already uses ‘On Behalf Of’ flows inside its own identity tools. Where an API or service can call another service on behalf of a signed-in user. But it’s only one company’s approach, and it’s about logging in and passing access around.
It doesn’t prove who someone represents outside the company.
Mapping the different zones for ‘On Behalf Of’
With OBO, we can now look at how roles change - both inside and outside the organisation.
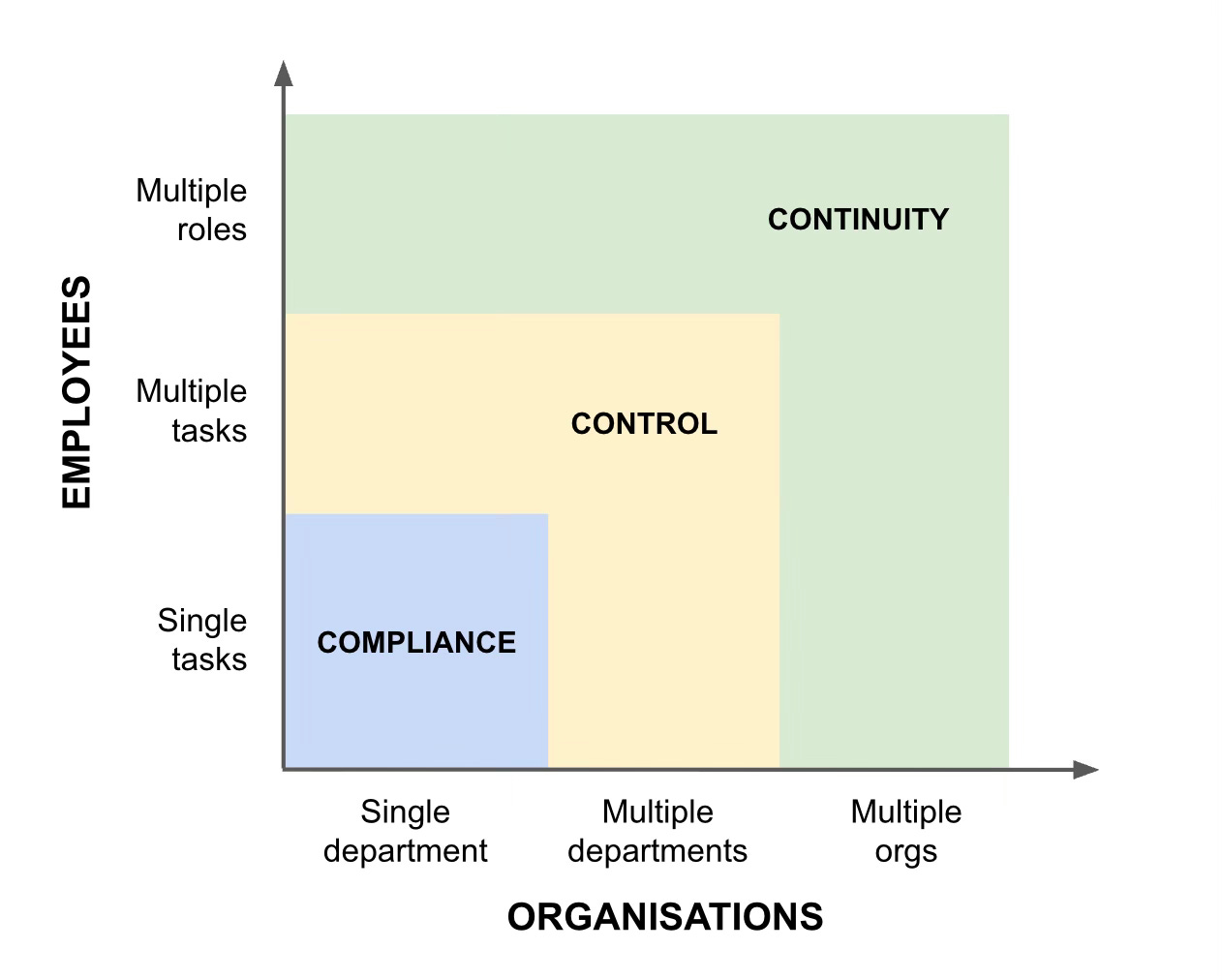
Let’s start with the simple case. Most businesses are set up to handle employee compliance around one person, one task, inside one company.
But what happens when employees move from handling a single task in a department, to managing multiple tasks? Or what if they need to represent the business across several different roles? Or act for multiple departments, or even several organisations?
It’s what Digidentity has been working on for years. Handling the risks around those employee transitions and transactions. Inside and outside the business.
When you map them all out, you can see how the ‘On Behalf Of’, or OBO, responsibilities change over time. And you can see how employees move across different ‘OBO Zones’.
The OBO Zones reflect the real-world progression of digital trust across different types of interaction.
For example, single tasks in single departments, much like IAM manages today, are about COMPLIANCE. We ask things like “Did we check the employee ID for this transaction?”
When an employee performs multiple tasks or across multiple departments, it’s about CONTROL. We must now ask things like “Is this person still authorised to act?”
And as the employee moves across multiple roles, or acts outside the business, it becomes about CONTINUITY. We must ask things like “Are we managing the risks of this employee’s digital signatures and external representations, and do it consistently over time?”
You all know the kind of thing that happens. An ops manager at a fast-growing business signs off on a supplier agreement using her digital signature. But it happens six weeks after moving into a new department.
The signature gets accepted, but no one checks if she is still authorised. Then, during an audit, the legal team discover she no longer has procurement authority, and the agreement has to be renegotiated under pressure. Costing precious time, lots of money, and their reputation.
These kinds of moments are never about fraud. They are just another accidental failure caused by a frictionless employee moment. With invisible assumptions and outdated records.
OK, so who in the business should be thinking about OBO?
Legal and compliance teams that need to manage employee risks, prove authority, and meet regulatory expectations
HR teams that need to ensure the employee experience reflects their real responsibilities
Operations and procurement departments that are responsible for protecting employee workflows involving approvals and external partners
IT and IAM leaders who need to evolve from ‘system access’ to portable, verifiable authority
Executives who need to understand how trust scales across the organisation, and how value is created and shifts across departments and people
From one-off access to portable authority
OBO won’t matter for every business in every sector.
But if your employees regularly need to prove things about themselves, or if they act on behalf of the business, then understanding and designing for ‘OBO’ is going to become critical.
The good news is that much of the ‘OBO stack’ is already in place:
Digital wallets to hold live OBO credentials
OBO certificates that bind the person, the organisation and the context
Authorisation flows that reflect real-time governance
Qualified eSignatures (QES) that deliver real accountability
So it’s time to map your OBO risks. Because you can’t manage what you haven’t made visible.
The OBO Zones give you a way to diagnose where your business is exposed, and where your identity and access management tools can’t reach.
Perhaps start where the stakes are highest. With employee ‘transactions and transitions’ like:
External signatures: who is representing the business, and what are they signing?
Cross-org approvals: who is authorised to sign things off externally, and how is that managed as people move and leave the business?
Regulatory-facing roles: who is dealing with regulators and compliance teams, and how are those interactions approved?
Once these OBO risks are understood, you can begin to move the business over to a model of dynamic trust. Where identity is portable, roles and businesses are verifiable, and authority can travel safely between people, systems, and organisations.
Because this is more than a theoretical concern about the future of digital ID and IAM.
It’s now a strategic shift in how businesses handle digital responsibility, delegation, and how they protect the business.
You see, OBO is already here. And it’s time to protect the organisation - and your employees - in the moments that matter.
In the coming posts, we’ll explore the ‘OBO Zones’ in more detail, and - you guessed it - how AI Agents are going to need OBO too.
And that’s a wrap. Stay tuned for more Customer Futures soon, both here and over at LinkedIn.
And if you’re not yet signed up, why not subscribe: